Blog
Featured posts
Federal Trade Commission Safeguards Rule
The fact is that any business that stores data about its customers should at least know what this rule contains because it will help when considering just how much exposure is too much.

From Phishing to Ransomware: Understanding and Countering Cyber Threats for Small Businesses
Prioritizing cybersecurity can no longer be an afterthought but must instead be prioritized as a critical necessity for safeguarding your business's assets, reputation, and future success.

Latest posts

Federal Trade Commission Safeguards Rule
The fact is that any business that stores data about its customers should at least know what this rule contains because it will help when considering just how much exposure is too much.
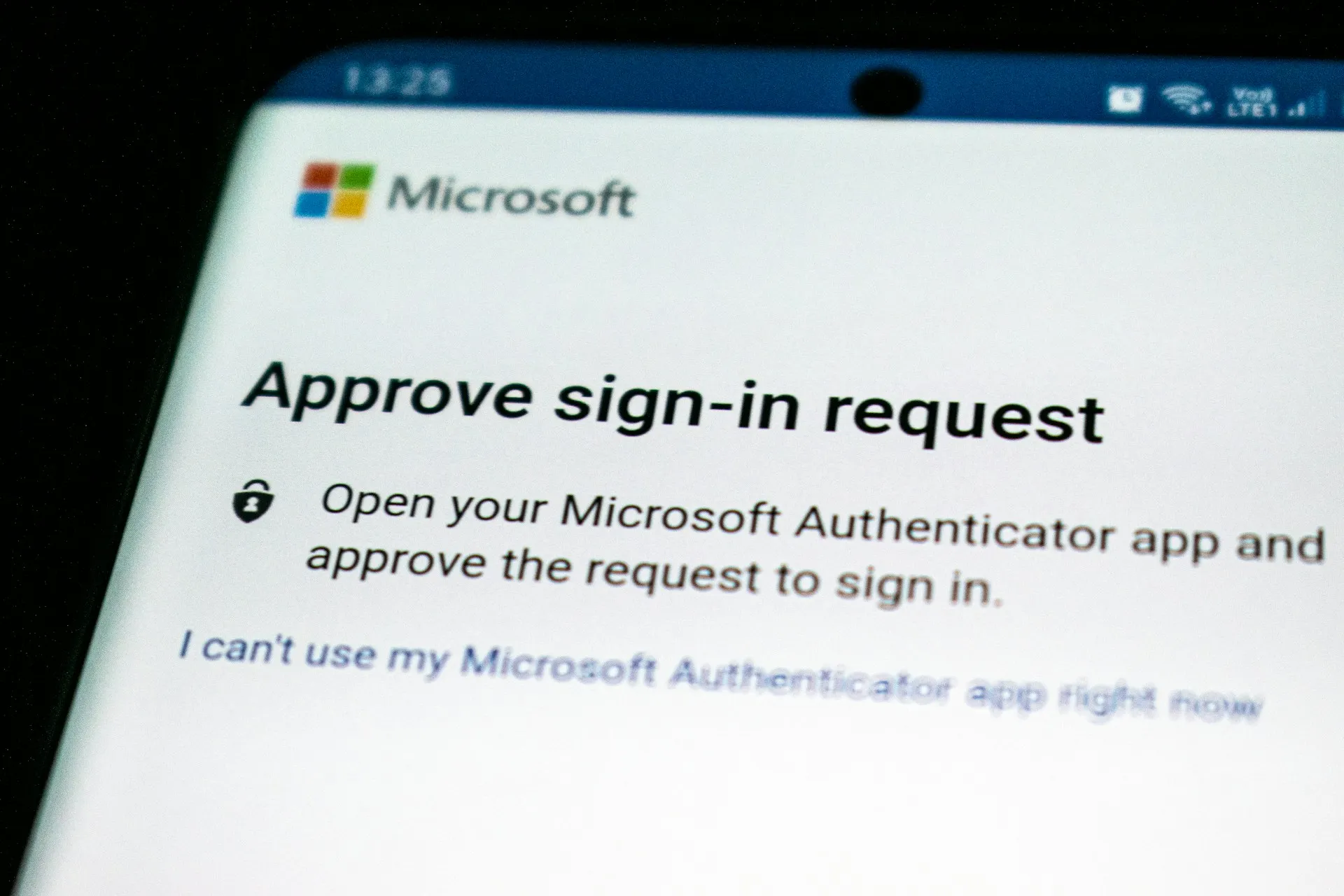
Maximize Cybersecurity for Small Businesses with Multi-Factor Authentication
Discover how Multi-Factor Authentication (MFA) can safeguard your small business against cyber threats and ensure compliance with FTC regulations.

From Phishing to Ransomware: Understanding and Countering Cyber Threats for Small Businesses
Prioritizing cybersecurity can no longer be an afterthought but must instead be prioritized as a critical necessity for safeguarding your business's assets, reputation, and future success.

Password Security for the Small Business
In the complex landscape of modern business operations, managing a multitude of strong, unique passwords across various accounts and platforms can quickly become overwhelming.

Getting old, wise, or possibly both
As our joints stiffen, in some ways so do our minds. Maybe that’s wisdom.
Let's work together!
Reach out to transform your ideas into action.
